
The world of cybercrime
Back in the days when the Internet was just beginning to explode, the stereotypical hacker was often portrayed as a hooded guy, working on his PC in a dark room to steal your data. In the modern world things get a little bit more complicated: often, cybercriminals do not act as single persons, but as groups of people with different skills and knowledge.
Cybercriminals mostly fall in one of these categories:
- Access broker – someone with good technical or soft skills (often both), specialized in getting access to accounts or infrastructures via hacking or social engineering, but all they do is sell the access to the highest bidder.
- RaaS operator – a Ransomware as a Service operator is someone who develops and maintains ransomware tools. They provide them to cybercriminals as a service, often taking some percentage from the ransom from cyberattacks. They are often the one negotiating with the victim of the attack as a proxy.
- RaaS affiliate – this the actual attacker who gets inside the infrastructure, looks through the network, moves laterally (getting more and more privileges and access) and in the end deploys the ransomware software.
- Script kiddies – this is a mocking term for an inexperienced hacker who only knows how to use already existing tools and scripts to gain access to IT systems.

With such vast gallery of rogues, it’s really important to properly secure your personal and organization data. Here are some of the best ways to do it:
1. Cyber hygiene
Cyber hygiene is a set of practices that organizations and individuals should perform regularly to maintain the security of their networks, devices, and data. Just like with your day-to-day personal security (e.g. locking the door of your home when you leave it), you need to develop similar habits for securing your data. Such habits can include: creating strong passwords, enabling multi-factor authentication where it’s possible, not providing your data to someone via phone or web forms, etc.
2. Gathering information about your assets
Before you can start defending your data, you need to identify what data you have and what is worth defending. In today’s world, it is almost impossible to defend every piece of data you or your company own. It is very important to do a proper assessment of the data/devices/systems you own and check what needs to be secured.
For example, a storage device inside your home network that stores your photos should have less priority in defending than your bank account. In terms of organization assets, it’s better to fully secure your core infrastructure that stores important data for the business than lose time on securing, for example, development environments.

3. Password management
Nowadays, credentials are often your “network perimeter”, especially if we are talking about services in the cloud. Leaked credentials are the top causes of data breaches and cyberattacks. So it’s really important to create strong passwords and store them in a safe place.
Some tips will help you create a strong password:
- The password should be at least 12 characters long
- Use a mixture of lowercase / uppercase letters, numbers, and special characters
- Don’t use words that can be found in dictionaries
- Don’t use your personal info in passwords (birth date, name, address etc.)
- Don’t use popular slogans or character strings (qwerty, P@sswd, 1234, etc.)
Strong passwords are often hard to remember, so they should be stored in a password manager, for example KeePassXC. It’s often a good idea to randomly generate them. KeePassXC and similar tools have a build-in password generator that will show you how strong your password (it’s mathematical entropy) is. If you need a strong but rememberable password, then the best option is to pick a quote or slogan (should be a sentence, not a single word) and then mix some upper/lowercase characters, numbers, and special characters in it.
A strong password can even save you when a data breach occurs, because almost always leaked credentials are hashed (encrypted) and the malicious actor needs to first crack them before he can use them. The stronger and more complex the password, the longer it will take to crack it.
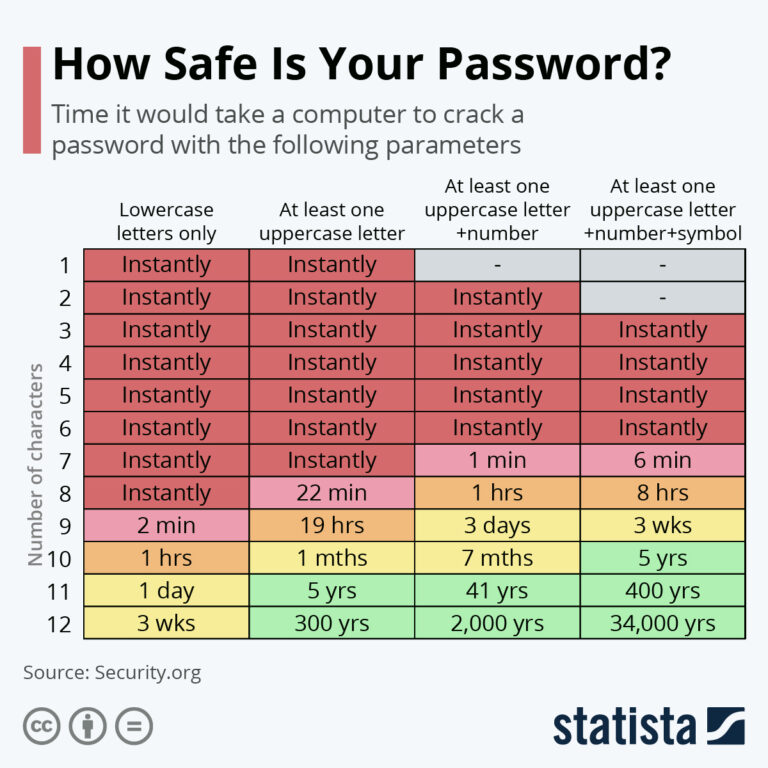
Image source: https://www.statista.com/chart/26298/time-it-would-take-a-computer-to-crack-a-password/
4. Defending from password attacks
Nowadays, many attack methods allow hackers to crack passwords and get into protected data or systems.
Some of them are:
- Brute-force attacks – a hacking method that uses a trial-and-error approach to crack passwords, login credentials, and encryption keys (testing every possible combination of characters and numbers)
- Dictionary attacks – a variety of brute force attacks, here instead of trying every possible combination, the attacker uses dictionaries (big txt files full of common words)
- Rainbow table attacks – a cracking method that uses special tables full of password hashes which are then compared to the hash of the password that someone wants to crack
- Password spray attacks – attacks where a malicious actor attempts the same password on many accounts before moving on to another one and repeating the same process.
To stay safe, make sure to follow these best practices to defend from password attacks:
- Have some system in place to lock accounts after a certain number of failed logins (e.g. fail2ban on Linux or Identity Protection services in AzureAD)
- Reset your passwords periodically or when you have a suspicion that they got leaked
- Always use multi-factor authentication when possible, it adds a second layer of security that can defend you even if someone can guess your credentials.
Multi-factor authentication is:
- Something you have (for example your phone)
- Something you know (your credentials or security questions)
- Something you are (biometrics)
5. Defending from phishing and social engineering attacks
In the context of IT security, social engineering is the psychological manipulation of people into performing certain actions or revealing confidential information.
Social engineering attacks include:
- Phishing – the most common type of social engineering, it’s a method that is based on sending fake emails / SMS (even sometimes voice calls) to a targeted person or a group of people. By this, the attacker wants to trick the person into giving out personal information or downloading infected files
- Pretexting – this type of attack involves a scenario (pretext) created by the attacker to lure victims into a vulnerable situation. The attacker often tries to impersonate someone that the victim trusts (or higher authority).
- Tailgating – in these types of attacks, someone without the proper authentication follows an authenticated employee (or private person) into a restricted area.
- Shoulder surfing – a simple technique, where the attacker tries to obtain some valuable information just by looking over the victim’s shoulder.
Unfortunately, there is no single good way to defend from social engineering. It is important to stay vigilant:
- Always double-check URLs in emails or while browsing the Internet:
- Always use HTTPS while connecting to websites (check if the website has a valid SSL certificate issued by a trusted organization)
- Always check the full address of the e-mail sender, not his visible name
- Look for spelling errors or bad grammar
- Use the Internet to find more information about the sender or the organization that he represents
- Double-check attachments in e-mails, never open them if they are suspicious (e.g. have strange extensions)
- Don’t give your valuable personal information to anyone via web forms or phone calls.

6. Check if your data was leaked
Many services let you check if your data was leaked. One of them is https://haveibeenpwned.com/, which shows you if your mail accounts were a part of some major data breaches and what data exactly was leaked. Additionally, you can configure an automatic notification for your accounts or even whole domains, so you can always stay up informed about the security of your data.
If you don’t want to use Haveibeenpwned there are other services like https://monitor.firefox.com/ which provide the same functionality.
7. Check the public exposure of your network / devices
It’s important to keep an eye on your private or organization network’s public visibility and keep it to a minimum. The best option would be to use some public search engines like Shodan (https://www.shodan.io/) or ZoomEye (https://www.zoomeye.org/). They use bots to scan and index publicly visible resources like IoT devices or servers with open RDP or SSH ports.
Additionally, you can use the Nmap tool (or Zenmap on Windows) to scan your public IP addresses to check what ports are visible and if your firewalls are configured correctly. Nmap can use a plugin that automatically checks if your servers or devices are vulnerable to some known exploits (it will automatically provide a link to the exploit descriptions + tips on how to protect against it).

8. Cybersecurity on the go
While traveling, it can be difficult to keep an eye on your cybersecurity. Follow these rules to reduce the risk of attacks:
- Always make sure that your devices are protected by passwords or biometrics
- Make sure that your devices are encrypted (e.g with Bitlocker)
- Never left them unattended in visible places
- Use an antivirus software
- Always stay up-to-date with OS and software updates
- Have your firewall enabled (with no ports open for public connections)
Special care should be taken when using public open WiFi networks. There is always a small chance that someone is using the network as a ground for cyberattacks like:
- Man-in-the-middle – it’s an attack where the hacker is secretly relaying and altering the communication between two hosts (e.g. redirecting you to a fake website)
- Evil twin – here the attacker is setting up a fake a WiFi hotspot with the goal of luring you to connect to it instead of the genuine one.
- Packet sniffing – this is a method that enables the attacker to collect and analyze network packets passing through the network. This is not harmful by itself, but it can be used to prepare the ground for later more serious attacks.
It’s generally a good idea to use a VPN when accessing private or organizational data on public WiFi networks. It creates an encrypted connection that hides your network traffic from other people in the network. If you don’t have access to VPN, you can simply use your phone’s cellular network (via hotspot or tethering) to create a private connection to the Internet.
Summary
Nowadays, keeping our data safe is becoming increasingly difficult. However, by using the information and advice above, you can increase your cybersecurity and significantly reduce the risk of successful attacks.
Jędrzej Boguszyński
IT System Administrator

